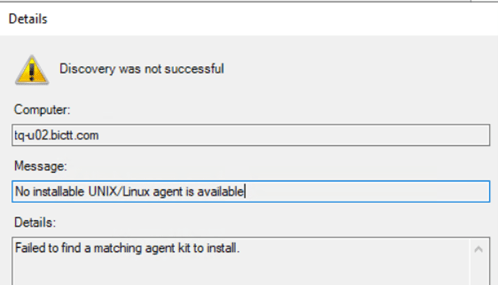
Runbook Designer and Deployment Manager crashing after applying Update Rollup 2 for System Center 2022 Orchestrator
We have updated the System Center 2022 Orchestrator to Update Rollup 2 few days back. After updating we tried creating a Runbook with the Get Alert activity of System Center Integration Pack for System Center – Operations Manager (SCOM) in Runbook designer as part of our internal activity. Everything was working as expected before the … Read more